 Computer users, beware; there’s an intrusive malware spreading across the Internet that’s capable of locking users out of their web browsers and redirecting them to fake IT support phone numbers. The hacker’s goal is likely to steal sensitive information from users, so it’s especially important that you don’t call this fake phone number.
Computer users, beware; there’s an intrusive malware spreading across the Internet that’s capable of locking users out of their web browsers and redirecting them to fake IT support phone numbers. The hacker’s goal is likely to steal sensitive information from users, so it’s especially important that you don’t call this fake phone number.
Little do users know that this is a simple phishing scam tactic that uses the guise of a technology issue to extort important information from them. Phishing scams usually involve spam email campaigns that come with viruses or malware attached to the message, or executes through a form. Thankfully, phishing emails are pretty easy to spot if you know what to look for, and once the email is identified as a scam, you can delete it or ignore it.
The malware in question will activate when you least expect it, and it’s practically impossible to simply ignore (not that you would want to anyway). It can hit your PC without warning, even if it’s while you’re visiting a secure website like Facebook or Google. Once the malware activates, you’ll see what looks like the blue screen of death from Windows PCs. You’ll then be shown a fake tech support message that urges you to contact a displayed phone number to resolve the issue.
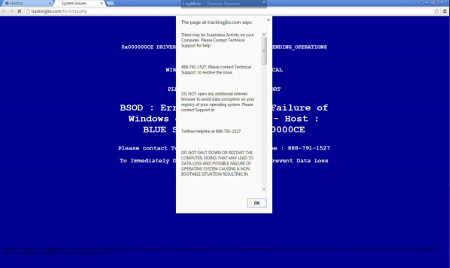
The blue screen can’t be closed out of or easily ignored; instead, the malware will completely freeze up the browser, leaving you with only two options to get rid of it. You could manually force the browser shut with the task manager (Ctrl+Alt+Delete), or restart your computer completely.
This kind of fear-mongering tactic is known as social engineering, a modern method for hackers who are trying to get past security measures by taking advantage of end-users. Social engineering attacks are designed to instigate an emotional response from the end-user, ranging from fear and frustration, to empathy and friendliness, depending on which medium the hacker is contacting the end-user from.
Having to use the aforementioned methods of bypassing this malware can have disastrous results, like causing downtime and deleting unsaved data. Furthermore, rebooting your system doesn’t guarantee that the malware is gone. If the malicious file is still on your computer, it will remain on the hard drive and could appear again at any moment. This is why, if you want to get rid of the malware for good, you need to eliminate the root cause of the problem by safely removing the infected file from your PC.
To reiterate; DON’T CALL THE PROVIDED PHONE NUMBER. The blog Delete Malware explains the risk: “If you call [the number] they won't actually remove adware from your computer. They will hijack your computer and steal all of your bank information and passwords. They are crooks, don't call them!”
Instead of relying on sketchy phone numbers in pop-ups on the website, you should contact the real IT professionals at (518) 203-2110. Calling a fake phone number is exposing your organization to the scam on a personal level. Hackers will take advantage of anyone who they think doesn’t know the slightest thing about IT-related issues like hacking attacks and social engineering scams, but it’s your organization’s unfamiliarity with your IT department that will really throw your business under the bus. Hackers want to instill confusion and panic in the hearts of your workers, which will ultimately lead to costly error.
Hackers posing as IT professionals isn’t an unheard-of concept. In fact, it’s one of the more common social engineering tactics that hackers try to pull off. Hackers count on your business’s employees to trust your IT support with sensitive information, making it a great cover for hackers… even if it’s spitting in the face of the legitimate IT professionals out there. You should make sure that your organization’s employees are familiar with your IT staff, as well as how to contact them if they need help. By doing so, you’ll be giving them contact information that they can cross reference for any potential social engineering hacks, like the “blue screen of death” malware.
By integrating proper monitoring and maintenance protocol for your business’s IT infrastructure, Evolve IT can help protect your business from hacks of all kinds, be it social engineering or more traditional campaigns. We can remotely locate and eliminate threats so that your organization can stay productive. Remember, you should only contact the real IT pros at (518) 203-2110 for any technology assistance.

